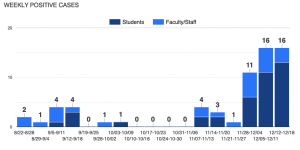
We expected to be somewhat back to normal during the Fall semester and it went by the wayside in late summer, so we prepared to continue a lot of what we did in the previous year in terms of masking, social distancing, limited interactions on campus and continued testing. Just when things started looking good in October, things went south. As you can see, after a lull, it shot up right after Thanksgiving and has stayed there. This is not unique to Wellesley, it is affecting so many other Higher Eds as well as it seems to be a national trend.
As if this is not enough to drain your energy, we had a couple of phishing attacks on campus this past week. Despite our best attempts to educate the community about protections against such attempts, several fell for this. These things take away valuable time for many of us to clean up!
And then we received the ominous notification about the log4j vulnerability. You can read where we currently are here. This was discovered on Dec 9th/10th timeframe and created havoc around the world. In short, log4j is a module that is used to log information when one connects to certain versions of a webserver software called Apache. This software is an open source software and is one of the most successful open source projects and the server is a brilliant creation that has grown in functionality over the last several years. This particular module is connected to versions of Apache that works with the programming language Java. The problem is that Apache is widely used, both by organizations downloading open source versions as well as by many commercial products. There are literally millions and millions of servers running this software.
The defect that was reported provides a hacker a way into your systems with enhanced privileges, one of which is access to a directory of all users, called LDAP (Lightweight Directory Access Protocol). Once enhanced access to this is established you can imagine what damage could potentially be inflicted.
The other problem is that there is no easy way to find out what are ALL the systems you use that have the defective version of the software, so that you can apply the suggested fixes. Whereas we can cover most, that is not enough. We need to detect ALL including software from other vendors that we use. This requires us to contact all of our vendors to make sure we are OK. And they are all scrambling and don’t have time to respond!
This again took a LOT of time away from so many of our staff for a few days. We have a virtual CISO (Chief Information Security Officer) whose team was very helpful in assisting us. As you can imagine, information security is a vexing cat and mouse game. Since a fix was put out, additional hacks related to log4j continue to emerge. Also, a fix for these kinds of systems is not as simple as Microsoft or Apple pushing critical fixes to other systems. In this case, it is only part of the solution. The other is a local configuration that each of us who run this need to adjust!
The blog post Understanding the Impact of Apache Log4j Vulnerability says
How long will it take for this vulnerability to be fixed across the entire ecosystem?
It’s hard to say. We looked at all publicly disclosed critical advisories affecting Maven packages to get a sense of how quickly other vulnerabilities have been fully addressed. Less than half (48%) of the artifacts affected by a vulnerability have been fixed, so we might be in for a long wait, likely years
There you have it!
BTW, sounds familiar? First when COVID was announced, the chaos, then vaccinaes came out, but not everyone took them and then the mutations kicked in and here we are. log4j is very similar, except, the time for solution has been far quicker than vaccines. But still, despite the solutions, so many millions of servers across the world remain vulnerable. And more variations on the theme are appearing every day…
I know, I know, I am beginning to look at everything happening as if they are similar to COVID crisis.
As if these are not enough to completely drain you, ransomware doesn’t want to go away. The most serious ones affecting common people happened recently. Kronos, a large Human Resources company that is used by many organizations for time tracking and paying employees was recently the victim of a ransomware attack. As someone who has been in the middle of similar crisis (not ransomware, but others), I understand the pressures the affected organizations face to release as much information as possible quickly. However, research to establish exactly what happened takes a LONG time and the worst thing you can do is to provide incorrect information too early or give too much information that would aid the perpetrators. This is happening with Kronos. Bottom line – so many were affected and Kronos told the clients that they will be down for weeks! And that everyone should resort to using paper until then.
These collectively have taken up so much time and effort over such a long time that there is a collective exhaustion in our organizations. Just when you feel that relief is on its way in some form, it seems to never come. I am so fortunate to have the best team I can hope for! We have been continuing to do some great things despite all of this, in addition to supporting our faculty, students and staff far more than before. The community’s reliance on technology and access to information electronically for library resources have gone up exponentially and we need to actively suppport them!
My own direct involvement in all of this and more is one of the reasons why I have not been able to write more blog posts than I have been able to! (Excuses, excuses, excuses!!!)
I want to thank LTS staff for all of their hard work and support for the past 2 years and the Wellesley community for adopting to constant changes in technology and access to information resources and their patience as we have had to attend to issues such as network connectivity issues.
Happy Holidays everyone, though I feel like “with all of this, what exactly does happy mean?”
Lots of praise for the Wellesley LTS team!