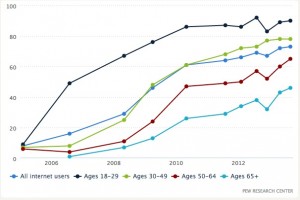
The technology transformations in the past 10-15 years has been remarkable. It is mostly driven by the internet, but there also have been several other advances in technologies that have helped accelerate research and development across the board. It has also leveled the playing field for many. For example, many authors and artists have been successful in directly reaching out to an audience through the internet that simply wasn’t possible before. The channels for success before the internet was limited, complicated and dismal.
But this also has resulted in a massive growth in the availability of information that are uncurated, biased, incorrect, so on and so forth. This has become such a huge problem that even for seasoned folks it is becoming impossible to identify whether some of what we see and read are true and accurate. One of the many horrifying examples is a recent horrifying story from India about a fake post that spread like wildfire through WhatsApp. Major technology companies like Google and Facebook continue to put in safeguards, but those intent on misusing the system bypass these immediately.
Everyone is busy producing new gadgets and monetizing the user base that no one seems to be investing enough in finding solutions for the long haul. They are busy finding bandaids and the blood appears to stop for a short period before gushing out!

 After a brief visit to
After a brief visit to